By Phillip Conrad, CCP, Lead CCA, & CMMC Consultant at Redspin
Introduction
To successfully complete a CMMC Level 2 assessment, the CUI environment must be scoped correctly. Doing so can make life easier, both when getting assessed (either via self-assessment or C3PAO assessment) and when conducting business involving CUI. Julie Andrews famously sang in The Sound of Music:
Let’s start from the very beginning
a very good place to start
When you read, you begin with A-B-C
When you sing, you begin with do-re-mi
And when you CMMC you begin with CUI-Sco-Ping. Okay, so maybe it doesn’t have quite the same ring to it, but it’s the best I could come up with. To be more precise, you begin by scoping the Controlled Unidentified Information (CUI) environment.
This post is for Department of Defense (DoD) contractors preparing for a Cybersecurity Maturity Model Certification (CMMC) Level 2 assessment and unsure where to start with defining their assessment boundary.
CMMC and the Role of Scoping
The 32 CFR Part 170 rule that went into effect in December 2024 implements the Cybersecurity Maturity Model Certification (CMMC) program.
Subsection 170.19(a) references the scoping requirement. 170.19(a)(1) states:
“The CMMC Assessment Scope must be specified prior to assessment in accordance with the requirements of this section. The CMMC Assessment Scope is the set of all assets in the OSA’s environment that will be assessed against CMMC security requirements.”
Additionally, subsection 170.19(c) says:
“Prior to performing a Level 2 self-assessment or Level 2 certification assessment, the OSA must specify the CMMC Assessment Scope.”
An OSA is an Organization Seeking Assessment. As an OSA, you will need to determine your assessment scope per the rule referenced above. The CMMC Level 2 Scoping Guide (version 2.13) will serve as a great resource in this effort.
The Scoping Guide outlines the following asset categories that you will assign to the assets in your CUI environment:
- CUI Assets
- Security Protection Assets
- Contractor Risk Managed Assets
- Specialized Assets
- Out-of-Scope Assets
Asset Treatment and Documentation
The Scoping Guide includes the following, listed under OSA Requirements:
“Document asset treatment in the System Security Plan (SSP).”
This got me thinking about what “documenting asset treatment” really means. For reference, this language was not included in the previous Scoping Guide (version 2.0).
An online search led me to this answer: documenting asset treatment involves identifying all assets within the system boundary, categorizing them, and outlining how they are protected. Having a data flow diagram and a network diagram will help inform the asset treatment of your in-scope assets.
As an OSA you will need to decide how each of these assets fits into your environment and if they are truly in scope.
Scoping essentially comes down to three questions when analyzing an asset:
- What do you have? (identifying all assets within the system boundary)
- What does it do? (categorizing them)
- Where is it? (outlining how they are protected)
Early versions of the Scoping Guide (like version 2.0) included a visual model for organizing assets in your CUI environment. I don’t know why it wasn’t included in the current Scoping Guide (version 2.13 as of this writing), but this figure (Figure 1) was provided in version 2.0 of the CMMC Level 2 Scoping Guide. It provides an organized example of how to visually present your assets in your CUI environment.
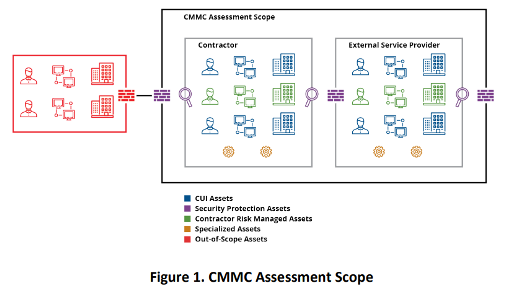
What Do You Have?
Start by identifying all the assets in the CUI environment. Ask and document:
- What assets come into play as CUI data enters, passes through, and exits your organization?
- What people, technology, and facilities are involved in the process of CUI data flow?
Another consideration is, do you have an External Service Provider (ESP) such as a Managed Service Provider (MSP) or Cloud Service Provider (CSP)? What is their involvement in the process?
What Does It Do?
Next, review your asset inventory and document how you would categorize each asset as it relates to the CUI environment.
- Does it process, store, or transmit CUI? Easy. It’s a CUI asset.
- Is it a Security Protection Asset (SPA), meaning, does it provide a security function within the assessment scope?
The Scoping Guide provides some examples:
- People (e.g. consultants, network admins)
- Technology (e.g. VPN services, SIEM solutions)
- Facilities (e.g. data center, SOC).
Also, consider the role of your MSP or CSP within the scoped environment. How does the CUI data flow between your organization and theirs? Developing a data flow diagram specifically for the CUI data will help provide clarity here.
Where Is It?
This question revolves around how the asset is protected.
- Is it located in a physically protected area such as in a secured server room or air-gapped environment?
- Is it logically protected, for example via network segmentation with access controls in place?
Create a network diagram to help identify where your assets are located and what category they sit in. A diagram modeled after the one in the earlier version of the Scoping Guide (the model in Figure 1 above) can be a helpful reference.
Scoping CUI – Prep Checklist
1. Identify where CUI enters, flows through, and leaves your environment. Map the lifecycle of CUI, from intake to output, to understand all touchpoints.
2. Conduct a full inventory of all people, technology, and facilities involved in the process of CUI data flow. This includes systems, users, devices, cloud environments, and physical locations.
3. Categorize each asset using the five CMMC asset types. Assign each asset as a CUI Asset, Security Protection Asset, Contractor Risk Managed Asset, Specialized Asset, or Out-of-Scope Asset.
4. Map your CUI data flow by creating a CUI-specific data flow diagram. Visualize how CUI moves between systems, users, and service providers.
5. Diagram your network to show where assets are and how they are protected. Include segmentation, logical boundaries, and access controls.
6. Determine which assets are in-scope and document the rationale. Clearly explain why each asset is or isn’t included in the assessment scope.
7. Update and include all scoping details and diagrams in your SSP. Make sure your SSP contains everything the assessors need to understand your environment.
Next Steps and How Redspin Helps
Now that you have a CUI data flow diagram and a network diagram of your scoped environment, include those in your System Security Plan (SSP). These diagrams will go a long way in assisting the CMMC assessment team with understanding your environment
Redspin is one of the most experienced and is the most trusted C3PAOs in the CMMC ecosystem. We’ve helped hundreds of organizations from large primes to small contractors prepare for their assessments, starting with scoping.
If you need help defining your CUI boundaries, identifying asset categories, or building your documentation, our experts can walk you through it all, make sure you are prepared for an assessment, and connect you with the right C3PAO!
Ready to get your CUI Scoping done right? Let’s connect.
Book a meeting to tackle CMMC with Redspin:
