Published 5.1.2024
Author: Tara Lemieux, CMMC Consultant, PA/PI/CCP/CCA/ISO Lead Auditor
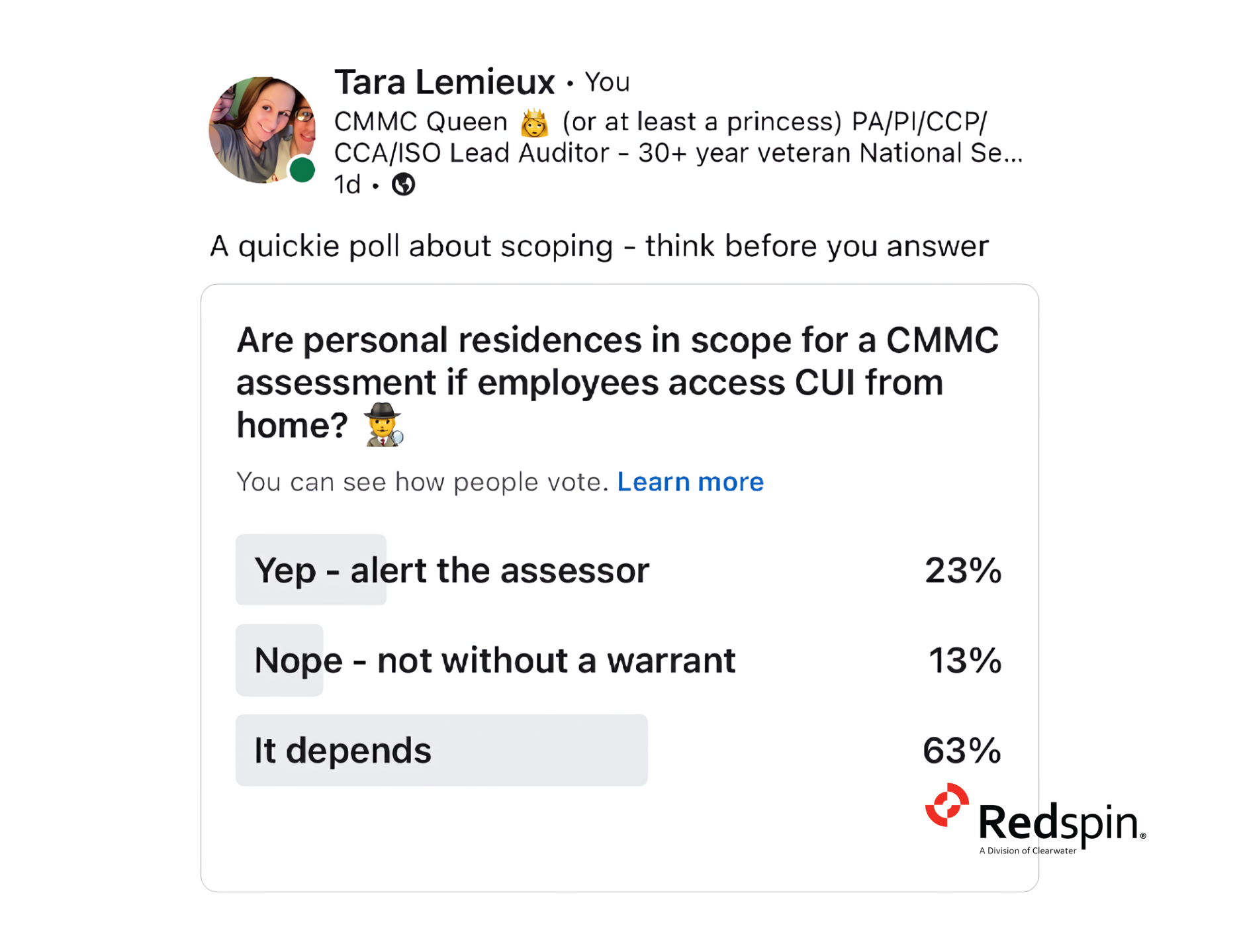
In a recent poll, participants were asked whether home office environments might fall within the scope of a CMMC assessment if the employee working from home processes, stores, transmits, or receives Controlled Unclassified Information (CUI). The 82 responses were, not surprisingly, widely varied; from a less certain, “it depends” (63%) to a more definitively resounding “YES” (23%). Some respondents went so far as to state, “Not without a warrant” (13%) – offering a unique view into the complexities and potential legalities surrounding our remote office environments. Employees may cite privacy as a primary concern, arguing that assessors shouldn’t have access to their personal space. Or, conversely, citing the security implications of allowing external parties to access their home networks and devices and fearing that this could ultimately expose them to potential breaches. Are these valid arguments? If so, how are they managed in the context of a CMMC assessment?
Also, why is there such uncertainty regarding whether these environments are in or out of scope? Aren’t the CMMC Scoping documents *the* authoritative guidance? If so, then scoping should be a relatively straightforward process – right?
Unfortunately, no – as context and circumstances matter. For example, is the employee utilizing a Virtual Desktop Environment (VDI) or similar technology? Are there any compensating controls to offset the risks associated with working from home? Finally, and perhaps most importantly, does the employee actually process, store, transmit, and/or receive CUI information or data? Or are they using secure methods (e.g. VPN to a client environment where the CUI resides) to access an environment or platform that hosts CUI data? Are there controls in place to prevent the employee from downloading, copying, or printing CUI?
Maybe scoping isn’t so straightforward after all.
Scoping—or determining which parts of an organization’s environment need to be assessed for cybersecurity compliance—is both critical and complex. Organizations are asked to ‘follow the data’ (in this case, CUI) to determine how it is interacting with our people, processes, workflows, devices, and components.
That sounds easy enough, however – as our survey shows, the application of this principle is not as straightforward as it seems. Especially for companies that have not yet developed a data flow diagram (depicting the flow of CUI through their organization) or an asset inventory (depicting which devices and components interact with this data) – making it nearly impossible to effectively establish our CMMC assessment boundaries.
For home offices, the requirements become even more nuanced. If an employee processes, stores, or transmits CUI from a home office, that space, including the network and devices used, typically falls within the scope of CMMC assessment. That said, and as previously discussed, it’s not always so cut and dry.
The CMMC Scoping Guides for Level 1 and Level 2 provide some basic direction for these scenarios. They outline how to identify the ‘CMMC Assessment Scope’—essentially following where the CUI data flows within the organization’s environment, including any segments where the data is stored, processed, or transmitted.
Knowing one’s environment is key, but knowing how the data we are entrusted to protect flows through this environment is critical. This includes understanding not just the physical and digital infrastructure but also the data types handled by the organization. Did you know that the CMMC Scoping Guides also provide specific handling instructions for various asset types? This includes CUI Assets, Security Protection Assets, Contractor Risk Managed Assets, Specialized Assets, and Out of Scope Assets. Not all asset types are subject to the same level of scrutiny.
From this perspective, we must map out all the touchpoints and data flows, thereby defining a scope that is both comprehensive and manageable. Regular audits and reviews of these scopes are necessary to adjust to any changes in the organization’s operations or threat landscape.
Consider a scenario where an employee works from a home office, using both company-issued and personal devices. Is the entire home network in scope? To determine this, one would need to evaluate where CUI is stored or accessed and how it is transmitted across the network. If the company-issued device has adequate security measures like a VPN and encryption, and CUI is never accessed through personal devices, only the company-issued device might be in scope. However, if personal devices access CUI or are connected to the same network as the company-issued device without adequate segmentation, then the scope could widen to include those devices and potentially the entire network.
Methods and Mechanisms for Effective Scoping
Effective scoping requires a multi-faceted approach:
- Asset Identification: Clearly identify and catalog all assets, including physical devices, software, and data repositories where CUI is handled. This step is foundational in defining the scope.
- Data Flow Mapping: Create detailed maps of how CUI data flows within the organization and beyond, including to remote environments like home offices. Understanding these flows helps pinpoint where protective measures are necessary.
- Risk Assessment: Regular risk assessments can reveal vulnerabilities and guide the adjustment of the scope to include emerging threats or changes in how data is handled.
- Segmentation: Use network segmentation to isolate sensitive information from less critical parts of the network. This can help minimize the scope and enhance security.
- Policy Enforcement and Training: Ensure that all employees understand the policies regarding the handling of CUI, especially in home office setups. Regular training and policy updates are crucial in maintaining security awareness and compliance.
Let’s apply these principles in a second commonly asked-about scenario. Imagine an employee using a home printer/scanner to print documents containing CUI. Is the printer considered in or out of scope? Does this mean a CMMC Assessor can visit my home to verify controls and compliance?
CMMC Control PE.L2-3.10.6: “Alternative Work Sites”
One of the key controls under CMMC Level 2 that directly impacts scoping, especially in the context of home offices, is control PE.L2-3.10.6, which addresses “alternative work sites.” This control speaks directly to our home office environments and our remote workers, requiring that the organization both define and enforce safeguarding measures for CUI at these work sites.
When considering home offices as alternate work sites, this control mandates a careful assessment and incorporation of security measures that provide these protections. This could include:
– Secure Connections: Ensuring that all connections back to the main office or data centers are securely encrypted, typically through VPNs.
– Physical Security Measures: Implementing measures to secure physical access to the home office, such as locked rooms or cabinets for storing sensitive documents or devices.
– Data Handling Protocols: Establishing strict guidelines on how to handle CUI in the home office, including rules for printing, storage, and destruction of sensitive data.
Let’s dig a little deeper to understand the possible implications of this control:
Suppose an employee at a home office often regularly prints CUI. In this case, the employee must ensure that the documents are securely stored in a locked space and that any copies are disposed of securely. This may influence our scoping decisions, however – does this mean an assessor will visit the employee’s home to confirm that the data is securely stored? Not necessarily, as there are different methods that an assessor may utilize to confirm secure storage – such as validating through interviews with the employee and confirming the controls are implemented correctly and operating as intended.
All of this highlights the need for comprehensive security measures for alternate work sites. By continuously assessing and reaffirming scope, organizations can enhance their security posture and ensure robust protection of CUI, even in less traditional work environments like home offices. This holistic approach to scoping not only aids in compliance with CMMC but also fortifies the organization’s overall cybersecurity defenses.
Finally, scoping is not a one-time task but an ongoing process that needs regular review and adjustment. The complexities involved, particularly with the increasing prevalence of remote work and home office environments, require a dynamic approach to ensure all aspects of data handling are secured. The scattered responses from the survey highlight the need for clearer guidelines, better training, and more effective tools to assist in scoping tasks, ensuring that organizations can confidently secure their CUI and comply with CMMC requirements.
So, are personal residences in scope for a CMMC assessment if employees access CUI from home? Well, as you’ve seen from our thorough exploration, it’s complicated. From asset identification and data flow mapping to risk assessments and security measures at alternative work sites, each aspect adds layers to our understanding. And if you’ve reached this conclusion feeling a tad overwhelmed, you’re not alone. Our poll results echoed this sentiment. Perhaps it’s time to go back to start, re-read from the top, and equip yourself with a magnifying glass—figuratively, of course. Let’s continue to unpack this jigsaw puzzle, one intricate piece at a time. Remember, we are here to help.
Through understanding and implementing effective scoping practices, organizations can better protect sensitive information and ensure they are prepared for CMMC assessments. Scoping should be seen not just as a preparatory step but as a crucial part of cybersecurity hygiene that plays a vital role in the overall defense strategy against cyber threats.
Do you have scoping questions?
Book a meeting to get CMMC certified with Redspin: