October 11, 2024 | 5 min read | Redspin Blog
CMMC 32 CFR
TL;DR CMMC 32 CFR:
-
-
-
- Failure to achieve and maintain the required CMMC level could result in losing the ability to accept DoD contracts at the time of award.
- CMMC is required for DoD contractors who store, process, or transmit sensitive information at different levels based on CUI and FCI sensitivity.
- Rollout will occur in phases, starting with Level 1 self-attestation and progressing to C3PAO assessments for Levels 2 and 3.
-
-
At long last, rule 32 CFR, formally establishing the Cybersecurity Maturity Model Certification (CMMC) program, is final. The rule is expected to become effective December 16, 2024, 60 days after its anticipated publication in the Federal Register on October 15, 2024. The Final CMMC program rule was released for public inspection on October 11, 2024.
This marks a significant milestone in the Department of Defense’s (DoD) efforts to validate its contractors’ cybersecurity measures for protecting sensitive information within the Defense Industrial Base (DIB). It also means the compliance clock is now ticking for DIB contractors and subcontractors.
“We’ve waited a long time for the 32 CFR for CMMC rule to be finalized,” said Brian McManamon, VP of Redspin. “This is a pivotal moment for the industry. Now that CMMC is officially here, we’re eager to continue assisting businesses as they navigate CMMC and ensure they are moving forward on their path with confidence, no matter where they are in the process.”
Key Takeaways from 32 CFR Publication of the Final Rule in the Federal Register:
- CMMC compliance is mandatory for contractors and subcontractors to receive and maintain DoD contracts.
- The rule features a simplified three-level structure, reduced from the originally proposed five levels.
- Contractors and subcontractors must adhere to DoD-approved DFARS and NIST-based cybersecurity standards.
- Service Providers in Scope: Cloud Service Providers (CSPs) and External Service Providers (ESPs) that handle Controlled Unclassified Information (CUI) must meet additional DFARS requirements, including FedRAMP compliance.
- The CMMC Program’s assessment phase-in plan, as described in 170.3, does not preclude entities from immediately seeking a CMMC certification assessment before the 48 CFR part 204 CMMC Acquisition rule is finalized and the clause is added to new or existing DoD contracts.
- Eligibility for Level 2 Contracts: To be eligible for a contract requiring a CMMC status of Level 2 (C3PAO), an Organizational Security Contractor (OSC) must have achieved either a conditional Level 2 (C3PAO) or a FINAL Level 2 (C3PAO) This means that organizations cannot participate in contracts requiring Level 2 CMMC unless they have undergone an official third-party assessment conducted by an authorized C3PAO and have obtained at least a conditional certification.
-
- It’s implied that if you don’t close out your Plans of Action & Milestones (POAMs) within 180 days, the conditional certification will be revoked, which could result in the loss of eligibility for contracts that require this level of compliance.
-
- With the finalization of 32 CFR and 48 CFR part 204, CMMC implementation will occur in four phases:
-
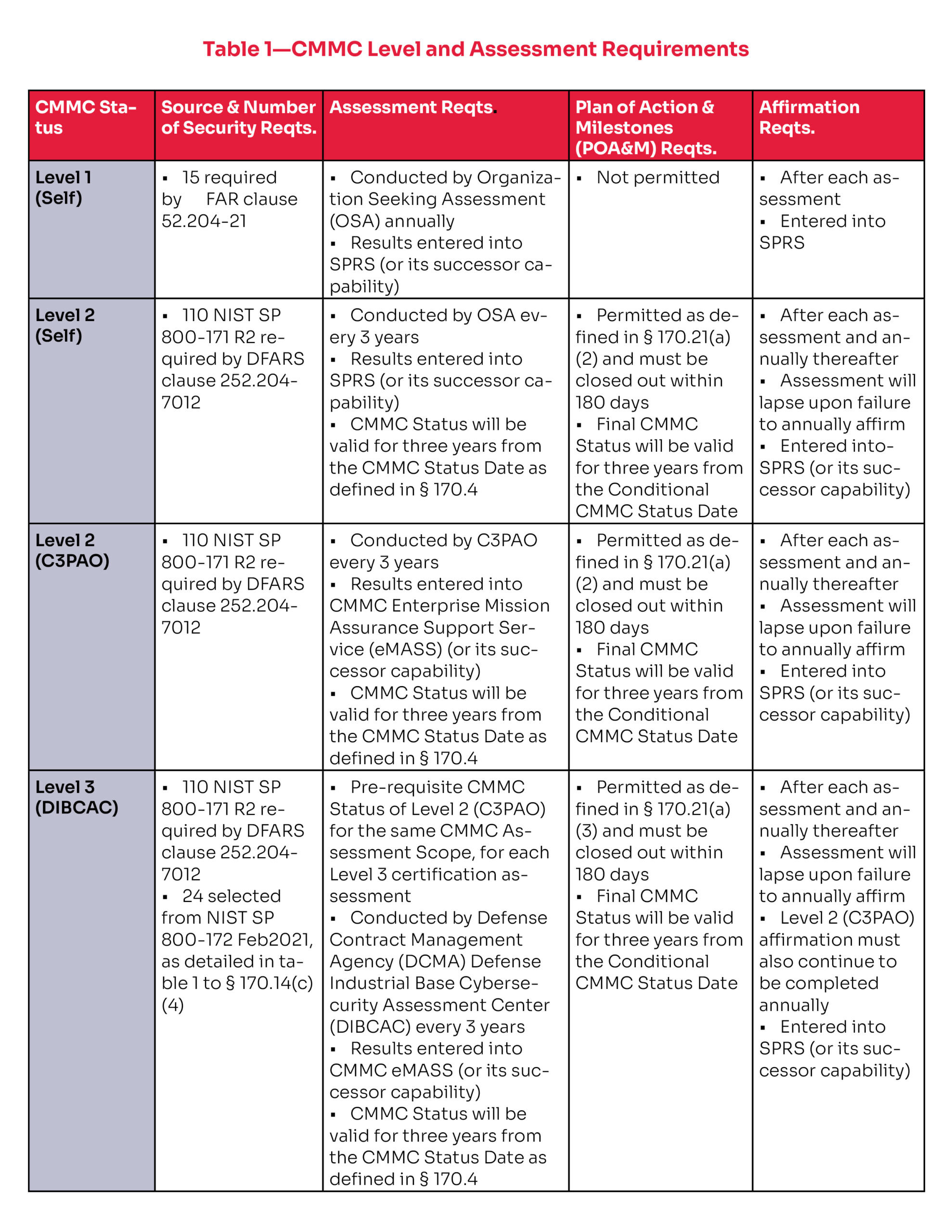
- Phase 1: Focuses on Level 1 self-assessments for contractors handling Federal Contract Information (FCI). This requires compliance with 15 security requirements outlined in NIST SP 800-171.
- Phase 2: Applies to contractors handling CUI, requiring Level 2 assessments. Compliance with all 110 NIST SP 800-171 controls is necessary. Some contractors may self-attest, while others will require a C3PAO assessment.
- Phase 3: Focuses on Level 3 certifications for contractors managing highly sensitive CUI, which necessitates DoD review and additional security controls.
- Phase 4: Represents full implementation across all DoD contracts
-
- Certified CMMC Assessors (CCA) Requirements: There must be two Certified CMMC Assessors (CCAs) per assessment team, excluding the CCA Quality Assurance (QA)
“The finalization of 32 CFR brings much-needed guidance and direction to the ecosystem,” says Tara Lemieux, author of The Guide to Everything CMMC. “At the end of the day, it’s important to remember that CMMC is about validating practices that DoD contractors should already be following. While these aren’t new, the significance of CMMC in safeguarding our nation’s data cannot be overstated.”
What Finalization Means for DIB Contractors
The finalization of 32 CFR has significant implications for prime contractors and subcontractors:
- Mandatory cybersecurity:
- Level 1: Requires 15 basic cybersecurity controls plus 2 additional requirements to protect Federal Contract Information (FCI), for a total of 17 requirements.
- Level 2: Requires 110 controls to safeguard Controlled Unclassified Information (CUI).
- Level 3: Adds enhanced controls designed to mitigate Advanced Persistent Threats (APTs).
- Validated compliance: Contractors and subcontractors must declare and demonstrate compliance through assessments and certifications.
- Subcontractor responsibilities: Prime contractors are responsible for ensuring that subcontractors handling FCI or CUI comply with the required CMMC level. This increases the need for communication and assessments across the supply chain.
- Potential contract loss: Failure to comply may result in losing existing and future DoD contracts.
- Phased implementation: Contractors should carefully monitor which phase applies to their contracts to ensure timely compliance.
What’s the Difference Between 32 CFR and 48 CFR?
While both 32 CFR and 48 CFR are related to CMMC, they serve different purposes:
- 32 CFR: Establishes the CMMC program, defines cybersecurity requirements, and outlines certification levels.
- 48 CFR: Outlines how CMMC requirements are included in DoD contracts and enforced in procurement processes. The proposed rule for 48 CFR was published in August 2024, is in a public comment period until October 14, 2024, and is expected to become final in 2025.
What Contractors Should Do Now
All DoD contractors must ensure compliance with the Defense Federal Acquisition Regulation Supplement (DFARS), particularly DFARS 252.204-7012, which covers the safeguarding of CUI. With the finalization of 32 CFR, contractors must also validate their compliance through a CMMC assessment, confirming adherence to DFARS and NIST standards. This includes defining boundaries for FCI and CUI.
By the end of the DoD fiscal year (September 30, 2024), contractors should have concrete action plans in place. This could involve self-attesting for Level 1 or scheduling third-party assessments for Levels 2 and 3.
CMMC requirements are already appearing in new Requests for Proposals (RFPs) and Requests for Information (RFIs). To stay on track, contractors should:
- Assess their security profile: Conduct an organizational-wide review to determine if CMMC certification is needed.
- Conduct a gap analysis: Identify where current cybersecurity measures fall short of the targeted CMMC profile.
- Foster collaboration: Ensure collaboration across legal, operations, finance, compliance, and privacy departments to integrate security into organizational culture.
- Remediate gaps: Develop actionable remediation plans and perform routine penetration testing to ensure controls function as intended.
- Ensure proper documentation: Maintain clear, concise documentation to demonstrate CMMC compliance.
- Partner with CMMC experts: Work with C3PAOs and specialists like Redspin for assessments and consulting services.
What about Joint Surveillance Voluntary Assessments (JSVAs)?
As the organization that has conducted the majority of JSVAs for CMMC across the ecosystem, here’s what we’ve learned so far about JSVAs now that 32 CFR has published.
- JSVAs Transition: For organizations that are not scheduled for a JSVA, assessments will be conducted under a regular CMMC assessment by Redspin moving forward. However, for those that have already scheduled their JSVAs, these will continue as normal under existing scheduled assessment dates.
- Converting DIBCAC-High to CMMC: For organizations that performed a straight DIBCAC-High certification, there is an opportunity to convert to CMMC This conversion process is expected to be primarily a paperwork shuffle, requiring additional hours to review the assessment reports and validate compliance.
- Looking Ahead: As we continue to assess the evolving CMMC rule, it may become necessary to provide a pricing quote for those organizations converting from DIBCAC-High to CMMC. We will be reviewing the rule and conducting further analysis to confirm any potential updates to this process.
Implementation Timelines
32 CFR
- Final rule publication: October 15, 2024
- Effective date: December 16, 2024
48 CFR
- Proposed rule published: August 15, 2024
- Public comment period ends: October 14, 2024
- Final rule: Expected 2025
Partnering with Redspin
Redspin, the first Authorized (and first to be recertified) CMMC Third Party Assessment Organization (C3PAO,) offers specialized services to guide contractors through CMMC assessments and compliance, ensuring they remain eligible for DoD contracts. Services include:
- Gap analysis, readiness, and consulting
- Managed services, through the Redspin Ready Managed Cloud Program, and managed security/Compliance Services
- Continuous compliance services to maintain readiness for future assessments
- CMMC training
By partnering with Redspin, contractors can confidently navigate the CMMC journey and maintain compliance with DoD requirements.
Stay tuned for more updates as we continue to follow and dissect the implications of CMMC’s final rulemaking. In the meantime, should you have any questions or need assistance with CMMC, Redspin is here to help. Please join our upcoming CMMC Connect session, contact us at info@redspin.com or fill out the form below to chat.
Book a meeting to get CMMC certified with Redspin:

