Blog
Welcome to our blog page, where you can stay up-to-date with all things CMMC and access information and best practices for protecting your organization’s sensitive data.

The Microsoft Windows Recall Feature: A Double-Edged Sword for Security and Privacy
Microsoft Windows Recall feature in Copilot Plua is powerful tool for productivity but has significant privacy and security concerns.
Navigating Temporary Deficiencies in FIPS 140-3 Validation for Updates to SPAs
Understand the significance of FIPS 140-3 validation for cryptographic modules and how it helps in meeting cybersecurity requirements.
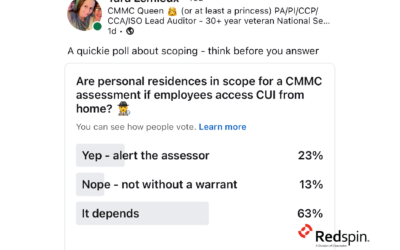
Not Without a Warrant: Why Is CMMC Scoping Such a Challenge?
Uncover the challenges of CMMC scoping: why determining the scope is crucial for assessing home office environments.
The CMMC Proposed Rule Published, What That Means for DoD Contractors
What the CMMC Proposed Rule means for DoD contractors.
CMMC 2.0, The Phased Approach
Redspin’s Director of CMMC Services, Robert guides you through the phased approach to CMMC implementation.
The CMMC Proposed Rule Is Here and Open for Public Comments
The long-anticipated Cybersecurity Maturity Model Certification (CMMC) proposed rule has been released and the public comment period is now open.
Setting the Record Straight: CMMC Timelines
Recent False Claims allegations against Verizon and Penn State University shed light on the DOJ Civil Fraud Initiative and future for federal contractors.
How to Prepare for a CMMC Interview
A guide to help team mates prepare for a CMMC assessment interview
CMMC Scoping: Charting the Course for Comprehensive Cybersecurity Assessments
What is CMMC scoping and why it is so critical?
Facing the Consequences: Recent False Claims Under the DOJ’s Civil Fraud Initiative and What This Means for Federal Contractors
Recent False Claims allegations against Verizon and Penn State University shed light on the DOJ Civil Fraud Initiative and future for federal contractors.
CMMC 2.0 How to Get Started on This Vital Journey
A C3PAO is a certified third-party assessment organization approved by Cyber AB to conduct CMMC 2.0 assessments for CMMC certifications.
Seizing the Moment: CMMC, the Urgency to Act Now
The urgency to act is not just about the immediate availability of JSVAP assessment schedule; it’s about positioning your organization for long-term success because once the CMMC rule becomes final, numerous organizations will be fighting for certification.
Unleashing Mayhem: The Terrifying Potential of HackRF One PortaPack H2 and Mayhem Firmware
This blog discusses the potential dangers of the HackRF One PortaPack H2 and its Mayhem firmware, which can be used for cyberattacks on critical infrastructure and defense contractors. It highlights the vulnerabilities of the U.S. supply chain and defense contractors and the need for increased awareness and countermeasures to protect national security.
Canada Jumps Into the CMMC Pond
In this blog, we cover Canada’s recent announcement of adopting the U.S. DoD CMMC program to enhance cyber protections for the Canadian supply chain.
The Time to Assess is Now, CMMC is On Track to Finalize in 2024
As of July 2023, CMMC has made it to the final rulemaking phase! It is expected to finalize 2024.
Deep Dive into CMMC Documentation: Ensuring Compliance & Clarity
A blog exploring the importance of proper documentation throughout a CMMC/JSVAP assessment.
Exploring NIST 800-171 Revision 3: Insights from a C3PAO
Redspin experts dive into the latest draft announcement of NIST 800-171 Revision 3 which is currently in the 60-day public comment period, highlighting the key updates and impacts to Organizations Seeking Certification (OSCs).
An Introduction to Redspin & CMMC
Dave Bailey and Rob Teague discuss the key aspects of CMMC certification and how Redspin, as one of the first organizations accredited as a C3PAO for the DoD, can help DIB suppliers meet their requirements.
The Key Roles of Documentation & Training
We explore two critical areas of the assessment process: documentation and training.
How GCC-High & a VDI Environment Can Help Clarify your Scope
How GCC-High and a VDI environment can help organizations meet CMMC requirements by providing a more secure and controlled environment for accessing and managing CUI.

Subscribe to our newsletter
Securing The Nation's Defense Industrial Base
Get started with Redspin Today
Helping you navigate CMMC.